This article continues my series on
my personal threat model for the internet. In this article, I'm
going to talk about the threat of automated attacks coming in to your
computer over the internet, while it is connected to the internet.
The basic problem underlying this threat is the same as that underlying threats #2 (malicious e-mail messages which attack your e-mail program) and #3 (malicious web pages which attack your web browser): the software you are running on your computer, which you need to do your job, play your games, or otherwise get value out of your computer, is full of bugs. Some of those bugs are security problems. The most dangerous type of security problem is one that allows some data which a program is reading, which is supposed to just be processed by the program, to overwrite portions of that program's memory such that it takes over the program. That data is then itself a program, and can take over your computer. Unfortunately, this type of problem is very common.
The first thing you need to do to protect against these threats is to regularly install security updates for your computer. On Windows you can do this by using Automatic Updates, on MacOS X it will be done for you by Software Update, and on Ubuntu, Update Manager.
When updates are available, make sure to install them as soon as you can! By the time an update is available, the problem that the update is intended to fix has often been made public already. The publication of the problem allows the update to be created in the first place, but it also allows malicious individuals to create attacks from it. The longer you wait, the longer you are vulnerable to problems which have been made public, and thus can be exploited by the largest population of attackers.
However, even if all of your software is fully up-to-date, it still isn't perfect. The general strategy for dealing with this type of problem, then, is to make sure that only data from sources you trust will ever be allowed into that software. This limits your exposure to attacks.
In later posts I'll talk about limiting your exposure to malicious data that you have specifically requested, but right now I'm just going to talk about preventing unsolicited data getting to your computer directly over the internet. The best way to do this is to get a commodity hardware router, and put it between your computer and the internet. Devices such as this are made by vendors such as linksys, belkin, buffalo or netgear.
You don't need to get a router with fancy "security" features like an "SPI firewall" or "intrusion detection". In my opinion these features don't add a lot - in fact, they will often cause difficult-to-diagnose problems for home users. Of course, the people who sell these devices love to put the word "security" on the box as many times as possible, but you really only need the most basic security feature, and that's the one that isn't really a "security" feature at all.
The basic feature that a router adds is a separate layer of protection, independent from anything you can do to your computer itself. If your home computer is hooked up directly to the internet, it looks like this:
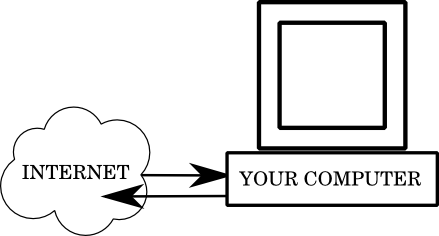
That is, whenever your computer tries to contact another computer on the internet, it sends a request directly via your modem. Whenever another computer tries to connect to you, it goes directly to your computer. This means that if there are programs that you don't know about, which your operating system vendor, or some application has left running on your computer, anyone on the internet will be able to access them.
If those programs were all perfectly secure, that would be fine. Unfortunately, programmers make mistakes, and mistakes lead to bugs, and bugs sometimes lead to security problems.
When you have a router, the picture looks more like this:
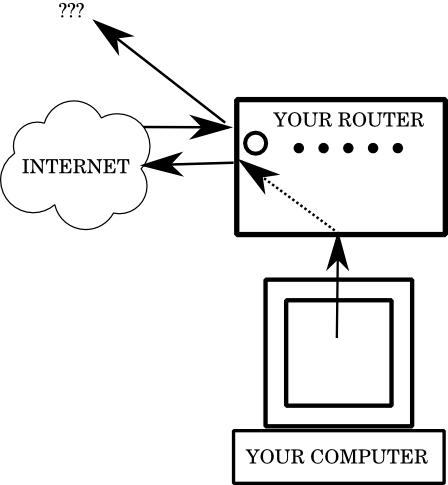
which is to say, when your computer submits a request to another computer on the internet, the router sees that the request is coming from inside the network, and transparently forwards it to the outside, establishing a channel of communication. However, when another computer tries to talk to the IP address that your ISP gives you, the device they find is the router. The router itself is a very simple device, and, unless you've done something unusual to it, will never be running any programs beyond the ones necessary to move traffic between you and your network. Because one of the functions of a router is to allow multiple computers on your home network, when connections come in from the internet, the router doesn't know which computer it should go to, even if you only have one. So the incoming connection will be refused, never having a chance to get to your computer.
This is preferable to running "firewall" software on your computer, for two reasons:
The basic problem underlying this threat is the same as that underlying threats #2 (malicious e-mail messages which attack your e-mail program) and #3 (malicious web pages which attack your web browser): the software you are running on your computer, which you need to do your job, play your games, or otherwise get value out of your computer, is full of bugs. Some of those bugs are security problems. The most dangerous type of security problem is one that allows some data which a program is reading, which is supposed to just be processed by the program, to overwrite portions of that program's memory such that it takes over the program. That data is then itself a program, and can take over your computer. Unfortunately, this type of problem is very common.
The first thing you need to do to protect against these threats is to regularly install security updates for your computer. On Windows you can do this by using Automatic Updates, on MacOS X it will be done for you by Software Update, and on Ubuntu, Update Manager.
When updates are available, make sure to install them as soon as you can! By the time an update is available, the problem that the update is intended to fix has often been made public already. The publication of the problem allows the update to be created in the first place, but it also allows malicious individuals to create attacks from it. The longer you wait, the longer you are vulnerable to problems which have been made public, and thus can be exploited by the largest population of attackers.
However, even if all of your software is fully up-to-date, it still isn't perfect. The general strategy for dealing with this type of problem, then, is to make sure that only data from sources you trust will ever be allowed into that software. This limits your exposure to attacks.
In later posts I'll talk about limiting your exposure to malicious data that you have specifically requested, but right now I'm just going to talk about preventing unsolicited data getting to your computer directly over the internet. The best way to do this is to get a commodity hardware router, and put it between your computer and the internet. Devices such as this are made by vendors such as linksys, belkin, buffalo or netgear.
You don't need to get a router with fancy "security" features like an "SPI firewall" or "intrusion detection". In my opinion these features don't add a lot - in fact, they will often cause difficult-to-diagnose problems for home users. Of course, the people who sell these devices love to put the word "security" on the box as many times as possible, but you really only need the most basic security feature, and that's the one that isn't really a "security" feature at all.
The basic feature that a router adds is a separate layer of protection, independent from anything you can do to your computer itself. If your home computer is hooked up directly to the internet, it looks like this:

That is, whenever your computer tries to contact another computer on the internet, it sends a request directly via your modem. Whenever another computer tries to connect to you, it goes directly to your computer. This means that if there are programs that you don't know about, which your operating system vendor, or some application has left running on your computer, anyone on the internet will be able to access them.
If those programs were all perfectly secure, that would be fine. Unfortunately, programmers make mistakes, and mistakes lead to bugs, and bugs sometimes lead to security problems.
When you have a router, the picture looks more like this:

which is to say, when your computer submits a request to another computer on the internet, the router sees that the request is coming from inside the network, and transparently forwards it to the outside, establishing a channel of communication. However, when another computer tries to talk to the IP address that your ISP gives you, the device they find is the router. The router itself is a very simple device, and, unless you've done something unusual to it, will never be running any programs beyond the ones necessary to move traffic between you and your network. Because one of the functions of a router is to allow multiple computers on your home network, when connections come in from the internet, the router doesn't know which computer it should go to, even if you only have one. So the incoming connection will be refused, never having a chance to get to your computer.
This is preferable to running "firewall" software on your computer, for two reasons:
- Firewall software is still running on your computer, and thus on your operating system. If your operating system itself has a flaw in it, the firewall can't protect you.
- Software which listens for incoming connections is doing so for a reason. Different components of the same program will sometimes communicate with each other over a network connection internal to the same computer - as a user of those programs, you really shouldn't need to know this. Firewall software will present you with prompts to allow or deny permission for programs: these prompts often boil down to "do you want this to work?" If you say yes, your computer will be exposed to a potential threat, if you say no, the program will break.




